권한관리
- 특정 유저나 ServiceAccount가 접근하려는 API에 접근 권한을 설정
- 권한 있는 User만 접근하도록 허용
- 권한제어
- Role
- 어떤 API를 이용할 수 있는지의 정의
- K8s의 사용권한을 정의
- 지정된 namespace에서만 유효
- verbs :
- create : 새로운 리소스 생성
- get : 개별 리소스 조회
- list : 여러 건의 리소스 조회
- update : 기존 리소스 내용 전체 업데이트
- patch : 기존 리소스 중 일부 내용 변경
- delete : 개별 리소스 삭제
- deletecollection : 여러 리소스 삭제
- RoleBinding
- User/Group 또는 ServiceAccount와 Role을 연결
- Role

< 이미지 출처 : [따배쿠/멤버십] 13-2. 인증과 권한 관리 - 권한관리편 >
Role 생성 및 부여
- 3. 인증과 권한 관리 - 인증편 이어서 진행
- Certificate Signing Requests 참고
- role 생성 및 확인
kubectl create role developer --verb=create --verb=get --verb=list --verb=update --verb=delete --resource=podskubectl get roleNAME CREATED AT
developer 2022-06-20T01:21:09Zkubectl create role developer --verb=create --verb=get --verb=list --verb=update --verb=delete --resource=pods --dry-run -o yamlapiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
creationTimestamp: null
name: developer
rules:
- apiGroups:
- ""
resources:
- pods
verbs:
- create
- get
- list
- update
- delete
- Role binding 및 확인
kubectl create rolebinding developer-binding-myuser --role=developer --user=myuserkubectl create rolebinding developer-binding-myuser --role=developer --user=myuser --dry-run -o yamlapiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
creationTimestamp: null
name: developer-binding-myuser
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: developer
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: myuser
- kubebernetes confing 파일에 등록 및 확인
kubectl config set-credentials myuser --client-key=myuser.key --client-certificate=myuser.crt --embed-certs=true
- context 추가
kubectl config set-context myuser --cluster=kubernetes --user=myuser
- myuser 추가 및 context 추가 확인
kubectl config viewapiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://10.100.0.104:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
- context:
cluster: kubernetes
user: myuser
name: myuser
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
- name: myuser
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
- myuser로 context 변경 및 확인
kubectl config use-context myuserkubectl config current-contextmyuser
- Role 확인
kubectl get servicesError from server (Forbidden): services is forbidden: User "myuser" cannot list resource "services" in API group "" in the namespace "default"
- Role, Rolebinding 삭제
kubectl config use-context kubernetes-admin@kuberneteskubectl delete rolebindings.rbac.authorization.k8s.io developer-binding-myuser
kubectl delete role developer
Cluster Role & Cluster Rolebinding
- 어떤 API를 사용할 수 있는지 권한 정의
- Cluster 전체(전체 namespace)에서 유효
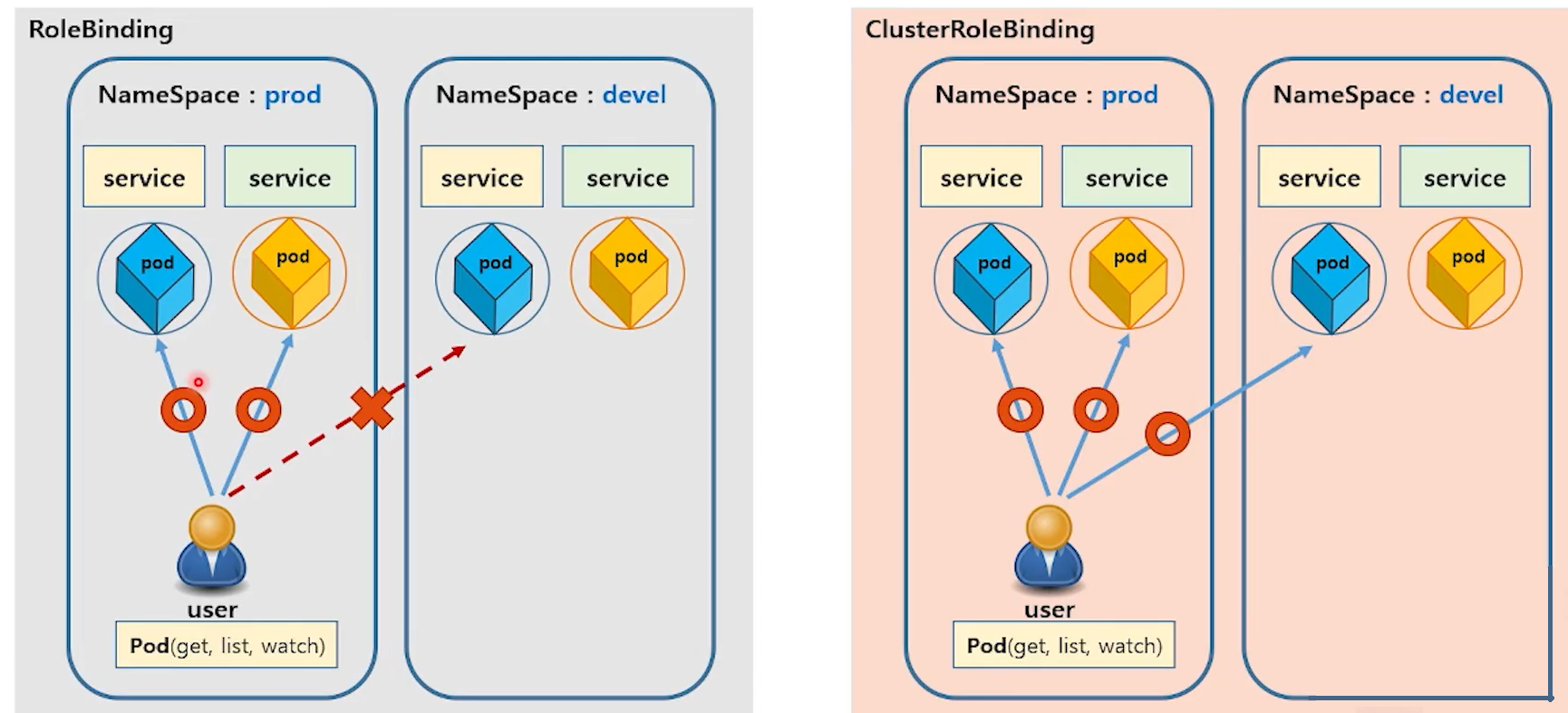
< 이미지 출처 : [따배쿠/멤버십] 13-2. 인증과 권한 관리 - 권한관리편 >
- Cluster role 생성
kubectl create clusterrole developer --verb=create --verb=get --verb=list --verb=update --verb=delete --resource=pods
- Cluster rolebinding 생성
kubectl create clusterrolebinding developer-binding-myuser --clusterrole=developer --user=myuser
- Context 변경
kubectl config use-context myuser
- Clusterrole, rolebinding 삭제
kubectl config use-context kubernetes-admin@kubernetes
kubectl delete clusterrolebindings.rbac.authorization.k8s.io developer-binding-myuser
kubectl delete clusterrole developer
- User 삭제
kubectl config delete-context myuser
kubectl config delete-user myuser
kubectl delete csr myuser
System이 지원하는 Clusterrole
kubectl get clusterroleNAME CREATED AT
admin 2022-06-16T07:41:21Z
cluster-admin 2022-06-16T07:41:21Z
edit 2022-06-16T07:41:21Z
kubeadm:get-nodes 2022-06-16T07:41:23Z
system:aggregate-to-admin 2022-06-16T07:41:21Z
system:aggregate-to-edit 2022-06-16T07:41:21Z
system:aggregate-to-view 2022-06-16T07:41:21Z
system:auth-delegator 2022-06-16T07:41:21Z
system:basic-user 2022-06-16T07:41:21Z
system:certificates.k8s.io:certificatesigningrequests:nodeclient 2022-06-16T07:41:21Z
system:certificates.k8s.io:certificatesigningrequests:selfnodeclient 2022-06-16T07:41:21Z
system:certificates.k8s.io:kube-apiserver-client-approver 2022-06-16T07:41:21Z
system:certificates.k8s.io:kube-apiserver-client-kubelet-approver 2022-06-16T07:41:21Z
system:certificates.k8s.io:kubelet-serving-approver 2022-06-16T07:41:21Z
system:certificates.k8s.io:legacy-unknown-approver 2022-06-16T07:41:21Z
system:controller:attachdetach-controller 2022-06-16T07:41:21Z
system:controller:certificate-controller 2022-06-16T07:41:21Z
system:controller:clusterrole-aggregation-controller 2022-06-16T07:41:21Z
system:controller:cronjob-controller 2022-06-16T07:41:21Z
system:controller:daemon-set-controller 2022-06-16T07:41:21Z
system:controller:deployment-controller 2022-06-16T07:41:21Z
system:controller:disruption-controller 2022-06-16T07:41:21Z
system:controller:endpoint-controller 2022-06-16T07:41:21Z
system:controller:endpointslice-controller 2022-06-16T07:41:21Z
system:controller:endpointslicemirroring-controller 2022-06-16T07:41:21Z
system:controller:ephemeral-volume-controller 2022-06-16T07:41:21Z
system:controller:expand-controller 2022-06-16T07:41:21Z
system:controller:generic-garbage-collector 2022-06-16T07:41:21Z
system:controller:horizontal-pod-autoscaler 2022-06-16T07:41:21Z
system:controller:job-controller 2022-06-16T07:41:21Z
system:controller:namespace-controller 2022-06-16T07:41:21Z
system:controller:node-controller 2022-06-16T07:41:21Z
system:controller:persistent-volume-binder 2022-06-16T07:41:21Z
system:controller:pod-garbage-collector 2022-06-16T07:41:21Z
system:controller:pv-protection-controller 2022-06-16T07:41:21Z
system:controller:pvc-protection-controller 2022-06-16T07:41:21Z
system:controller:replicaset-controller 2022-06-16T07:41:21Z
system:controller:replication-controller 2022-06-16T07:41:21Z
system:controller:resourcequota-controller 2022-06-16T07:41:21Z
system:controller:root-ca-cert-publisher 2022-06-16T07:41:21Z
system:controller:route-controller 2022-06-16T07:41:21Z
system:controller:service-account-controller 2022-06-16T07:41:21Z
system:controller:service-controller 2022-06-16T07:41:21Z
system:controller:statefulset-controller 2022-06-16T07:41:21Z
system:controller:ttl-after-finished-controller 2022-06-16T07:41:21Z
system:controller:ttl-controller 2022-06-16T07:41:21Z
system:coredns 2022-06-16T07:41:23Z
system:discovery 2022-06-16T07:41:21Z
system:heapster 2022-06-16T07:41:21Z
system:kube-aggregator 2022-06-16T07:41:21Z
system:kube-controller-manager 2022-06-16T07:41:21Z
system:kube-dns 2022-06-16T07:41:21Z
system:kube-scheduler 2022-06-16T07:41:21Z
system:kubelet-api-admin 2022-06-16T07:41:21Z
system:monitoring 2022-06-16T07:41:21Z
system:node 2022-06-16T07:41:21Z
system:node-bootstrapper 2022-06-16T07:41:21Z
system:node-problem-detector 2022-06-16T07:41:21Z
system:node-proxier 2022-06-16T07:41:21Z
system:persistent-volume-provisioner 2022-06-16T07:41:21Z
system:public-info-viewer 2022-06-16T07:41:21Z
system:service-account-issuer-discovery 2022-06-16T07:41:21Z
system:volume-scheduler 2022-06-16T07:41:21Z
view 2022-06-16T07:41:21Z
weave-net 2022-06-16T07:42:05Z
- view는 system에 존재하는 대부분의 resource를 get, list, watch 가능
kubectl describe clusterrole viewName: view
Labels: kubernetes.io/bootstrapping=rbac-defaults
rbac.authorization.k8s.io/aggregate-to-edit=true
Annotations: rbac.authorization.kubernetes.io/autoupdate: true
PolicyRule:
Resources Non-Resource URLs Resource Names Verbs
--------- ----------------- -------------- -----
bindings [] [] [get list watch]
configmaps [] [] [get list watch]
endpoints [] [] [get list watch]
events [] [] [get list watch]
limitranges [] [] [get list watch]
namespaces/status [] [] [get list watch]
namespaces [] [] [get list watch]
persistentvolumeclaims/status [] [] [get list watch]
persistentvolumeclaims [] [] [get list watch]
pods/log [] [] [get list watch]
pods/status [] [] [get list watch]
pods [] [] [get list watch]
replicationcontrollers/scale [] [] [get list watch]
replicationcontrollers/status [] [] [get list watch]
replicationcontrollers [] [] [get list watch]
resourcequotas/status [] [] [get list watch]
resourcequotas [] [] [get list watch]
serviceaccounts [] [] [get list watch]
services/status [] [] [get list watch]
services [] [] [get list watch]
controllerrevisions.apps [] [] [get list watch]
daemonsets.apps/status [] [] [get list watch]
daemonsets.apps [] [] [get list watch]
deployments.apps/scale [] [] [get list watch]
deployments.apps/status [] [] [get list watch]
deployments.apps [] [] [get list watch]
replicasets.apps/scale [] [] [get list watch]
replicasets.apps/status [] [] [get list watch]
replicasets.apps [] [] [get list watch]
statefulsets.apps/scale [] [] [get list watch]
statefulsets.apps/status [] [] [get list watch]
statefulsets.apps [] [] [get list watch]
horizontalpodautoscalers.autoscaling/status [] [] [get list watch]
horizontalpodautoscalers.autoscaling [] [] [get list watch]
cronjobs.batch/status [] [] [get list watch]
cronjobs.batch [] [] [get list watch]
jobs.batch/status [] [] [get list watch]
jobs.batch [] [] [get list watch]
endpointslices.discovery.k8s.io [] [] [get list watch]
daemonsets.extensions/status [] [] [get list watch]
daemonsets.extensions [] [] [get list watch]
deployments.extensions/scale [] [] [get list watch]
deployments.extensions/status [] [] [get list watch]
deployments.extensions [] [] [get list watch]
ingresses.extensions/status [] [] [get list watch]
ingresses.extensions [] [] [get list watch]
networkpolicies.extensions [] [] [get list watch]
replicasets.extensions/scale [] [] [get list watch]
replicasets.extensions/status [] [] [get list watch]
replicasets.extensions [] [] [get list watch]
replicationcontrollers.extensions/scale [] [] [get list watch]
ingresses.networking.k8s.io/status [] [] [get list watch]
ingresses.networking.k8s.io [] [] [get list watch]
networkpolicies.networking.k8s.io [] [] [get list watch]
poddisruptionbudgets.policy/status [] [] [get list watch]
poddisruptionbudgets.policy [] [] [get list watch]
- cluster-admin는 전체 resource에 대해 모든 권한을 다 가짐
kubectl describe clusterrole cluster-adminName: cluster-admin
Labels: kubernetes.io/bootstrapping=rbac-defaults
Annotations: rbac.authorization.kubernetes.io/autoupdate: true
PolicyRule:
Resources Non-Resource URLs Resource Names Verbs
--------- ----------------- -------------- -----
*.* [] [] [*]
[*] [] [*]
'INFRA > DevOps' 카테고리의 다른 글
| [k8s] Storage emptyDir 및 share volume (0) | 2023.03.20 |
|---|---|
| [K8s] Storage 개념 및 hostPath (0) | 2023.03.14 |
| [K8s] 인증과 권한 관리 - 인증편 (1) | 2023.02.27 |
| [K8s] Cordon& Drain (1) | 2023.02.20 |
| [K8s] Taint & Toleration,Cordon& Drain (0) | 2023.02.13 |




댓글